What are network protocols? A complete guide

Incalculable quantities of data flow from device to device and network to network on a daily basis, and every single transmission follows a very specific set of rules and standards.
Those rules and standards are known as network protocols. They define the ways in which devices communicate and exchange data across networks, playing an integral role in how the internet works, from email to cybersecurity and everything in between.
What is a network protocol?
Put simply, network protocols are sets of rules that dictate how devices communicate with one another, more specifically, how data is sent, received, and interpreted.
There are various types of network protocols, each overseeing a specific aspect of network communications. Some handle data transmission, others manage addressing and routing, while some focus on security and error detection.
Why are network protocols important?
Network protocols are what make all forms of digital communication possible.
Without network protocols, there would be no standardized way for devices to exchange data safely and efficiently. Entire systems, including private networks and the internet itself, would be unable to function, and networks, as we know them, would simply not exist. They link billions of devices across the globe, facilitating processes like email, file downloads, streaming, and web browsing.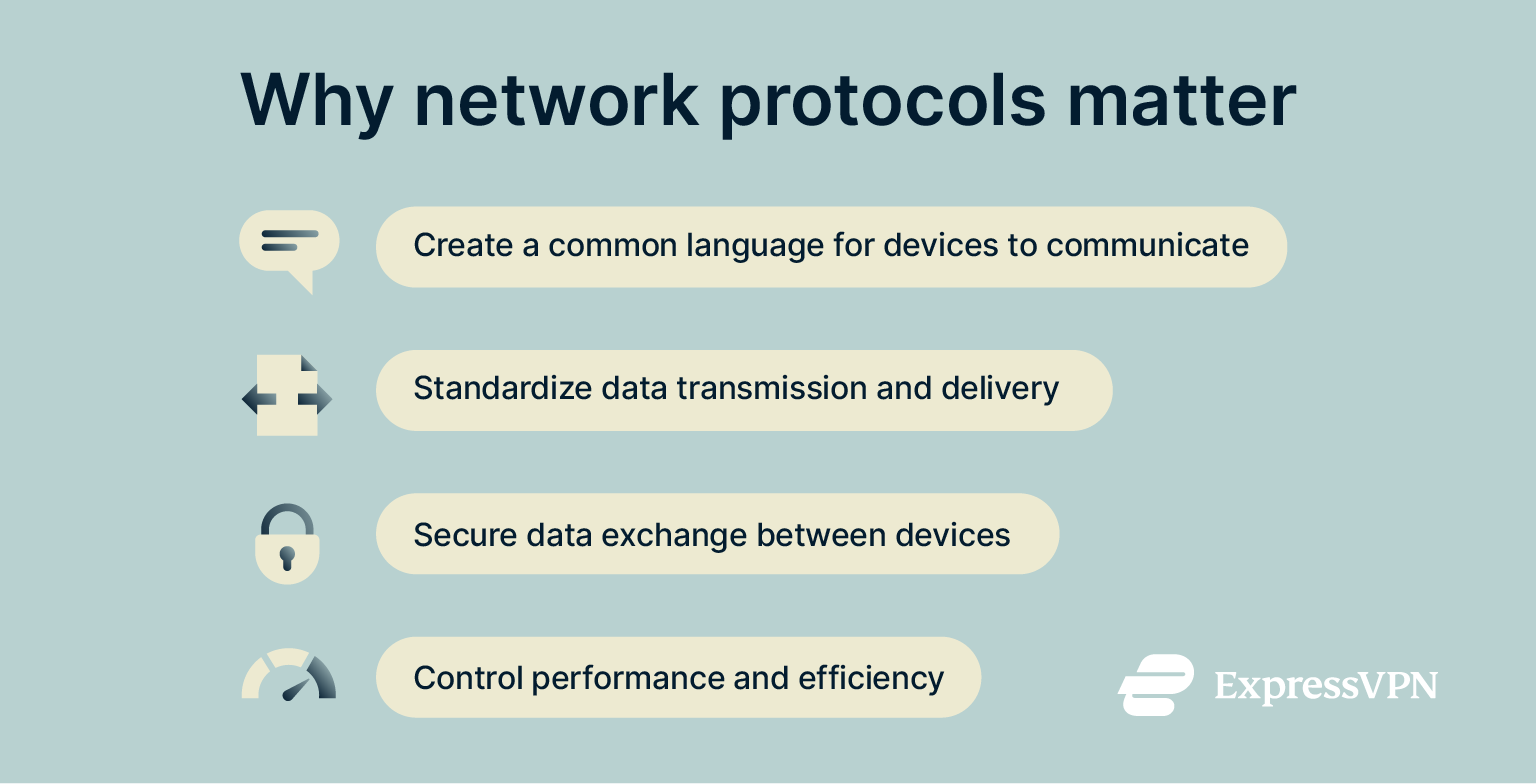 Here are just some of the core benefits network protocols bring to the table:
Here are just some of the core benefits network protocols bring to the table:
- Establishing a common language between devices: Network protocols allow different devices made by various manufacturers to communicate with one another, despite having completely different operating systems and designs.
- Standardizing data delivery: Protocols control the flow of data, ensuring that it’s always processed, handled, sent, and received according to an established framework. This helps to minimize the risk of errors or incomplete transmissions.
- Securing data exchange: Security-centric network protocols safeguard data as it flows from device to device, protecting it from various kinds of cyberattacks, like Domain Name System (DNS) spoofing.
- Influencing performance and efficiency: Protocols also influence the speed and efficiency at which data moves across networks. Some are made to function as fast as possible to keep latency down, while others involve additional steps and complexity for safer exchange but slower speeds.
Who uses network protocols?
Almost everyone uses network protocols, to some extent or another. If you have a digital device and that device connects, shares, or communicates in any way, whether it’s with a printer, the internet, or the cloud, you’re using network protocols.
You rely on them to access this webpage, for example, and you use them every time you browse the internet, send an email, download or upload files, or carry out numerous other online activities. You need them to carry out any sort of digital communication.
Meanwhile, those who interact with networks on a professional basis, like IT specialists and network administrators, engage with network protocols more directly. They use them to manage, develop, and secure the networks they oversee. Unfortunately, cybercriminals, too, can use and exploit network protocols to carry out their attacks, like spreading malware or gaining access to users’ devices without their consent.
How do network protocols work?
At the simplest level, network protocols work by creating a set of rules that every participating device follows when sending, receiving, and interpreting data.
When one device sends information, network protocols divide the data into small pieces called packets, label them with destination addresses, and transmit them across the network. The receiving device uses protocols to reassemble the packets, check for errors, and deliver the data to the correct application.
When you open a website, for example, the Hypertext Transfer Protocol (HTTP) or Hypertext Transfer Protocol Secure (HTTPS) protocols tell your browser how to request and receive the web page data, while the Transmission Control Protocol (TCP) and Internet Protocol (IP) protocols ensure that the right data is found and travels correctly and in full to the right destination.
Rules for data transmission
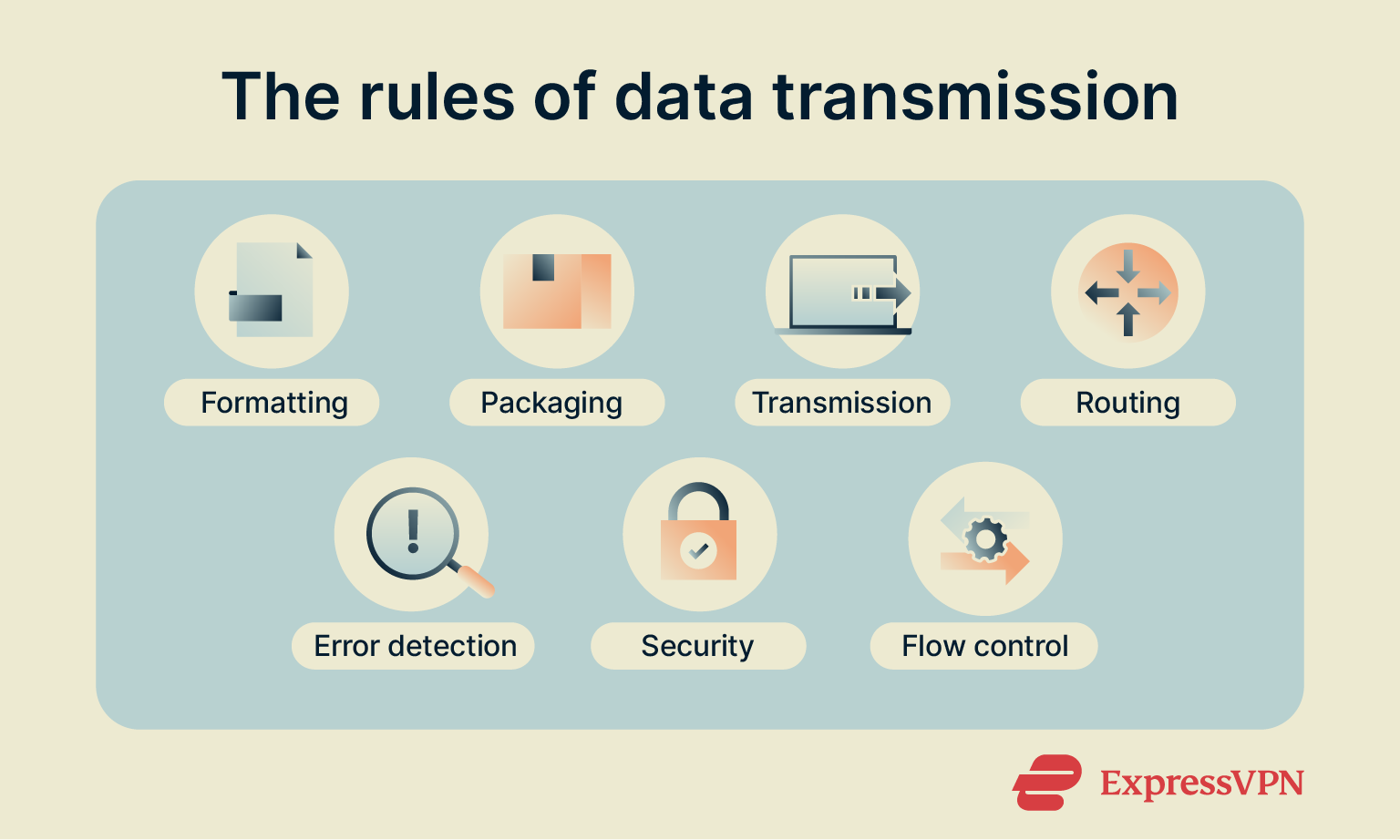 During data transmission, network protocols manage every step of the process based on standardized rules. The specific rules and functions can vary by protocol but generally include areas such as:
During data transmission, network protocols manage every step of the process based on standardized rules. The specific rules and functions can vary by protocol but generally include areas such as:
- Data formatting: Organizes information, such as text and images, into a digital structure that all devices can understand.
- Data packaging: Dictates how data is split into individual chunks, or “packets,” and how they’re labeled in preparation for transmission, such as adding individual sequence numbers and destination information.
- Data transmission: Controls how data flows across networks to other devices. These rules dictate the order in which packets are sent, for example.
- Addressing and routing: Decides which path data should take from one network to another and how devices at each end of the transmission should be identified and verified.
- Error detection and correction: Establishes how devices should spot errors during data transmissions, like incomplete data deliveries, and take the necessary steps to correct them.
- Security: Ensures that data remains secure and private while it’s transmitted from device to device, with the aid of methods such as encryption, authentication, and secure handshakes.
- Flow control: Controls how much data is sent at once in order to maximize efficiency and avoid overloading the receiving network.
Main types of network protocols
There are thousands of different network protocols in existence, but they can largely be categorized into three main groups: communication, management, and security. Here’s a closer look at what these groups entail, along with some examples for each one.
Communication protocols
As the name implies, communication protocols control how devices communicate with one another. They help devices establish connections and exchange data, and they also play a vital role in allowing devices to access the internet. Numerous online services, including email, instant messaging, and file transfers, all rely on communication protocols to function.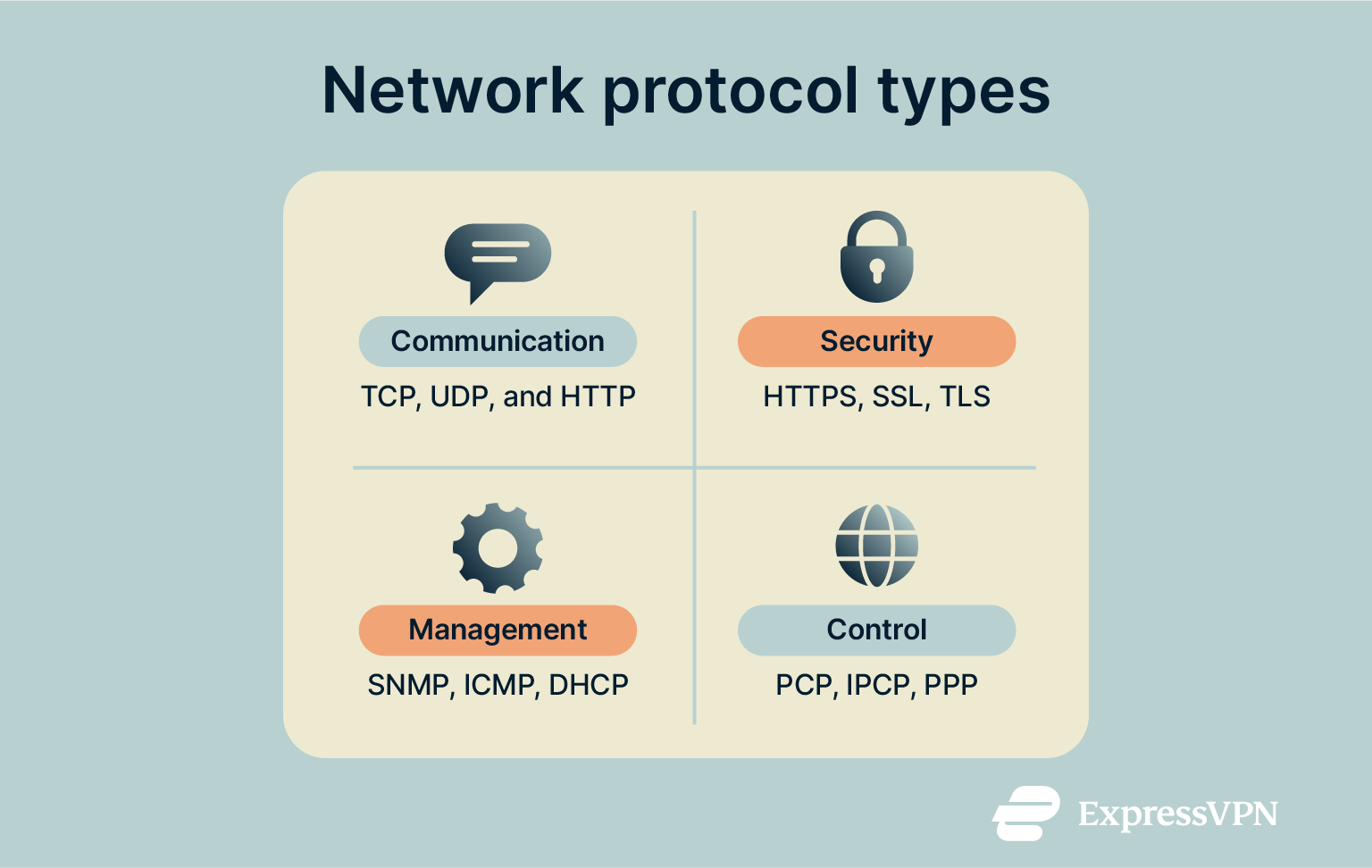 Examples include:
Examples include:
- Transmission Control Protocol (TCP): Arguably the most important communication protocol, TCP provides reliable and errorless data transmission between devices.
- User Datagram Protocol (UDP): A connectionless protocol that’s faster than TCP since it doesn’t establish a connection prior to sending data but is more prone to errors.
- Hypertext Transfer Protocol (HTTP): An application layer protocol used in web browsing to transfer data between web servers and browser applications.
- Remote Desktop Protocol (RDP): Allows users to remotely connect to and control another computer over a network.
- File Transfer Protocol (FTP): Transfers computer files into binary and text formats for transmission between clients and servers on the same computer network.
Network security protocols
These protocols are responsible for establishing the necessary standards and systems to keep data safe as it travels from place to place. They serve to encrypt data and block unauthorized users from being able to access it, and they play a vital role in cybersecurity and secure, private communications between network devices.
Well-known examples of security protocols include:
- Hypertext Transfer Protocol Secure (HTTPS): The secure version of HTTP, this protocol uses either Secure Sockets Layer (SSL) or Transport Layer Security (TLS), usually the latter, to encrypt web data.
- Secure Socket Layer (SSL): A cryptographic protocol used to encrypt sensitive data and internet connections for server-client and server-server communications.
- Transport Layer Security (TLS): The successor to SSL (and a more secure and efficient option), TLS encrypts data between communicating applications.
- Internet Protocol Security (IPsec): A suite of security protocols providing authentication of encryption of data transmitted over IP networks.
Management protocols
Network management protocols dictate the rules for how computer networks should be managed in order to optimally use their resources and avoid problems and disruption. They control processes like establishing and maintaining stable connections between devices, as well as identifying and resolving any errors that might arise.
Commonly used protocols include:
- Simple Network Management Protocol (SNMP): Helps network administrators manage network devices, monitor performance, and spot technical issues.
- Internet Control Message Protocol (ICMP): Used mainly for sending error messages and running basic network diagnostics, like the ping command.
- Dynamic Host Configuration Protocol (DHCP): Allocates IP addresses to devices as they connect to a network, as well as providing subnet masks and DNS addresses.
- Address Resolution Protocol (ARP): Links IP addresses to physical machine addresses, known as Media Access Control (MAC) addresses, on local networks.
- Network Basic Input/Output System (NetBIOS): Manages session connections between applications on different devices, allowing them to communicate over a local network.
Control protocols: Key functions and examples
The term “control protocols” is less specific than the other three and may cover some of the aforementioned protocols from the other categories. It refers to any protocols that control how data move from one place to another, rather than carry the actual content (like files, videos, or emails).
These protocols are in charge of details like when to send data, how fast to send it, and what to do if something goes wrong.
They help:
- Establish connections between devices
- Manage the flow of data so networks don’t get overloaded
- Ensure successful delivery by checking that data reaches the right destination
Examples include TCP, as well as the Port Control Protocol (PCP), which allows devices to communicate with upstream routers to tell them how to forward incoming traffic, and the Internet Protocol Control Protocol (IPCP), which is used for configuring IP over point-to-point protocol (PPP) connections.
How protocols enable interoperability
Network protocols let different operating systems and devices (like routers) talk to each other by standardizing the rules for communication, regardless of their underlying design and code. By following the same standards, Windows PCs, for example, can communicate with Apple Macs or Android smartphones without any issues or barriers between them.
To make this kind of interoperability possible, protocols don’t operate on their own. Instead, they work in coordinated groups called “protocol suites.” Each protocol in the suite handles a specific task, like routing, delivery, or security, and together they ensure data moves smoothly from one device to another.
The most widely used example is TCP/IP, the suite that forms the foundation of the internet.
Real-life example: TCP/IP in action
TCP and IP are two of the most significant network protocols, and that’s because they work together to handle the two most essential parts of any online communication: addressing and delivery.
IP is responsible for assigning IP addresses to devices so data can be addressed and routed correctly, while TCP handles the delivery of data and connections between devices.
Here’s a simple step-by-step breakdown of how this all works:
- IP lookup: You type a web address into your browser and hit ‘Enter,’ initiating an IP address lookup via the DNS, which is a core piece of internet infrastructure that translates human-readable, text-based web addresses into numerical IP addresses.
- TCP handshakes: Once the correct IP address is found, TCP handshakes take place to form a connection between your device and the relevant web server and confirm that they’re both ready to communicate.
- Data encapsulation: The relevant data is broken down into packets and labeled with its sequence number and destination.
- Data transmission: Data packets are transmitted across the network to the destination IP address. TCP controls the flow to ensure efficient use of network resources and prevent congestion.
- Reassembly: Once all the data packets arrive, they are reassembled into the original data stream and effectively handed over to the relevant application to be presented to the user.
The OSI model and protocol layering
The Open Systems Interconnection (OSI) model is a conceptual representation of how the internet works. It’s divided into seven distinct layers, each representing a different aspect of network functionality.
Network protocols are involved in each of those layers, providing the framework for the various stages of data transmission.
Overview of the 7 OSI layers
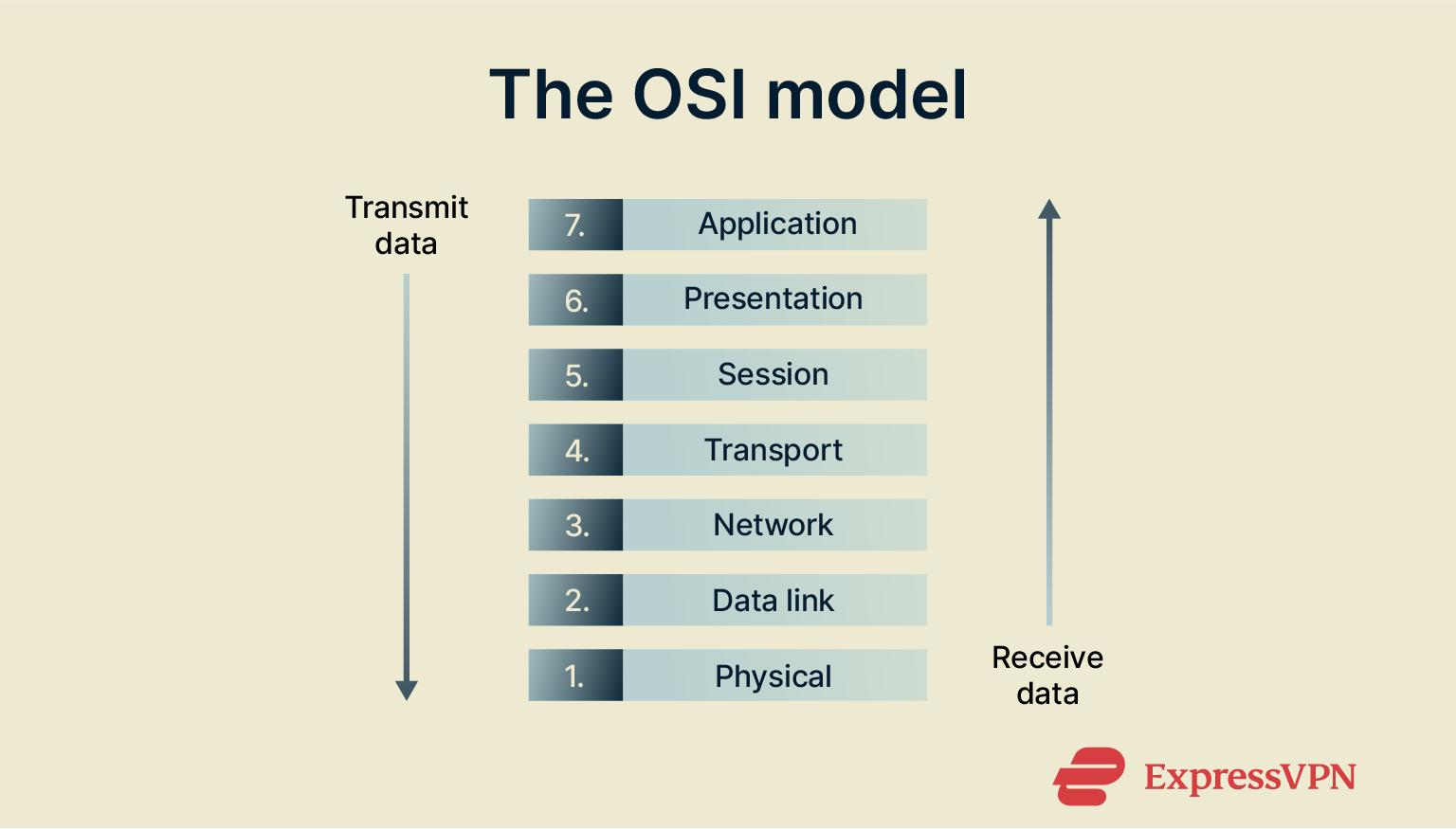 The seven layers of the OSI model are as follows:
The seven layers of the OSI model are as follows:
- Physical: Represents the physical components and media that transmit raw bits of data, such as cables, switches, and Wi-Fi signals. Protocols don’t apply at this layer because it deals only with signals, not communication rules.
- Data link: Defines how data is packaged into small chunks called frames and transferred between devices on the same network, with built-in methods for detecting and correcting simple errors. Relevant protocols at this layer include PPP and ARP.
- Network: Revolves around data routing and forwarding. In other words, it looks at the ways in which ideal, optimal paths are found and selected for data to travel through. Common protocols here include IP and IPsec.
- Transport: Covers how end-to-end communication works between devices and how errors in the data transmission process can be identified and fixed. The key protocols at this layer are TCP and UDP.
- Session: Explores how communication channels are managed between computers that wish to connect and exchange data with one another. Relevant protocols include NetBIOS and RPC.
- Presentation: Represents how data is translated into a usable, understandable format for the end user. Common protocols include SSL and TLS.
- Application: This final layer represents how data finally reaches end-user applications and services. Typical protocols at this layer include HTTPS and FTP.
OSI vs. TCP/IP: Key differences
So far, we’ve looked at TCP/IP as a set of network protocols that handle IP address designation and data delivery across networks.
But TCP/IP can also refer to a network model, just like OSI, which divides network communications into different layers, albeit in a more practical and condensed way.
There are several core differences between the two.
Firstly, the OSI is a purely conceptual model, mainly used for educational purposes. The TCP/IP model, meanwhile, is more practical, developed by the U.S. Department of Defense to enable communication across interconnected networks.
The TCP/IP model is also more condensed, with just four layers compared to OSI’s seven. The four layers featured in TCP/IP are:
- Link: Explores how initial connections are formed between networks and devices.
- Internet: This layer controls addressing and routing of data across different networks.
- Transport: Covers the actual transmission of data from place to place.
- Application: The user-facing layer, receiving data and providing relevant services for applications to function.
A simple way to think of the two models is that the OSI is conceptual and theoretical, almost like a blueprint of how the internet works, while TCP/IP actually shows the official, functional architecture that powers it all.
Network protocols in cybersecurity
As mentioned earlier, a whole group of network protocols are focused on security, dictating processes like encryption and authentication to help data flow more securely and privately where it needs to go. Unfortunately, cybercriminals can also exploit weaknesses in network protocols to launch their attacks.
How attackers exploit protocols
Cyberattackers can take advantage of the predictable, structured way in which network protocols work to exploit networks and pieces of internet infrastructure. They can use attacks like ARP and DNS spoofing, for example, to manipulate trust and reroute online traffic, or TCP session hijacking to intercept unencrypted data communications. Attackers may also exploit misconfigured or outdated protocols, like old versions of FTP.
How to secure your network protocols
Enforcing encryption, authentication, and data integrity checks across all of your communication layers is one of the most effective ways to instantly secure your network protocols.
It’s also wise to move on from outdated or legacy protocols, like Telnet, which allows users to log into other devices on the same network remotely, and opt for more secure, modern alternatives, like Secure Shell (SSH), which provides encrypted connections between computers for remote access.
Keep all relevant software and firmware up to date, too, and install the most secure VPN protocols and other security protocols on core network devices, like routers.
Recommended tools and practices for securing protocols
A wide range of protocol security and network monitoring tools can help you secure your protocols and gain the data you need to identify and address vulnerabilities. Network administrators should look into protocol and port scanning solutions, along with encryption validation systems. Security information and event management (SIEM) platforms can also help you monitor and log network data, while firewalls and intrusion detection systems should help you block or detect unauthorized users.
Applications of network protocols
As mentioned, network protocols are indispensable in almost every possible form of digital communication. Their applications are varied and numerous, and countless everyday users, businesses, and IT specialists rely on them daily.
Everyday use cases (web, email, file transfer)
Every day, billions of internet users rely on network protocols to allow them to access websites in their browsers, search the web, download and upload files, send emails to their friends and families, and enjoy other online activities, such as streaming, online gaming, and live video chats. HTTP and HTTPS, for instance, regulate browsing, while protocols like SMTP control how emails travel from sender to recipient.
Enterprise and infrastructure applications
In the world of business, protocols provide the necessary foundations for the secure and reliable data transfers that power various business operations. As well as the core protocols that every user benefits from, like TCP and IP, corporate networks often involve specialist, business-oriented protocols, such as:
- SSH and VPN protocols for secure remote access to corporate resources and networks.
- SNMP and ICMP for monitoring traffic and detecting issues.
- Remote Authentication Dial-In User Service (RADIUS) and Kerberos for verifying user identities and controlling access.
- Border Gateway Protocol (BGP), Open Shortest Path First (OSPF), and similar protocols that define how data moves between sites.
Protocols in IoT and smart devices
More and more devices are powered by network protocols nowadays, like the Internet of Things (IoT) and smart devices. Given the fact that these devices sometimes lack the high-end processing power of computers and similar devices, they often use scaled-down, specialized protocols to establish connections and communicate with routers and networks. Examples include Message Queuing Telemetry Transport (MQTT) and Constrained Application Protocol (CoAP).
Troubleshooting and performance tips
Everyday users won’t generally need to worry too much about getting “behind the scenes” of network protocols. However, network specialists and technicians, as well as enterprise IT teams, may need to troubleshoot networking issues and reconfigure protocol settings to optimize performance for their devices.
Common protocol errors explained
Network administrators often encounter recurring problems that occur during or because of protocol communication, such as:
- Timeouts, which are often related to packet loss or congestion on the network.
- Connection resets, sometimes caused by firewalls blocking traffic.
- DNS failures, often linked with misconfigured DNS servers or DNS caching issues.
- Handshake errors due to incompatibilities in security certificates or cipher suites.
How to monitor network protocol performance
IT professionals and network engineers can use an array of network monitoring tools to track network performance. These tools can monitor and log statistics about latency, bandwidth, throughput, handshake completion times, and other important metrics, all of which can help to paint a picture of network performance and identify recurring errors or weaknesses.
FAQ: Common questions about network protocols
What are the 10 types of network protocols?
There are more than 10 types of network protocols, but 10 well-known examples include the Transmission Control Protocol (TCP), Internet Protocol (IP), Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol Secure (HTTPS), File Transfer Protocol (FTP), Dynamic Host Configuration Protocol (DHCP), Simple Network Management Protocol (SNMP), Internet Control Message Protocol (ICMP), Secure Sockets Layer (SSL), and Address Resolution Protocol (ARP). Each of these protocols serves its own distinct function, with TCP controlling how data is divided into packets and transmitted between networks, for example, and HTTPS adding a secure layer of encryption to web page data.
What are the 4 main types of protocols?
The main categories of network protocols are communication protocols, network security protocols, and management protocols. There are also control protocols that can include protocols from the other three categories. Each group has its own role, with communication protocols defining how network devices communicate with one another and security protocols acting to keep networks, devices, and data safe from cyberattacks or unauthorized access.
What is a protocol with 3 examples?
In networking, a protocol is simply a set of rules or instructions that set out how networks should function when communicating with one another or exchanging data. Well-known examples include the Transmission Control Protocol (TCP), which controls the transmission of data from one point to another; the Simple Mail Transfer Protocol (SMTP), which is used for sending emails; and the Hypertext Transfer Protocol (HTTP), which controls how web browsers and servers communicate and exchange information.
How do network protocols affect data transmission?
Network protocols set out the rules and standards for how data should be formatted, encapsulated, encrypted, transmitted, sent, and received by network devices. They define every detail of how data moves from place to place, including how it should be broken down into individual packets, how those packets should be formatted, and how they are delivered to precise destinations.
What’s the difference between communication, security, and management protocols?
Each of these groups of network protocols has its own distinct purpose, and all three are important for networks to function. Communication protocols control how devices interact and exchange data, security protocols focus on protecting (encrypting) data, and management protocols control network operations and resource allocation.
What protocols do routers use?
Routers primarily use a range of routing protocols that facilitate communications between the routers themselves and other network devices. Examples of routing protocols include the Routing Information Protocol (RIP) and Open Shortest Path First (OSPF), which both focus on helping routers find and use the optimal path for data to follow.
How do network protocols make the internet work?
Network protocols provide the necessary rules that allow data to move in a secure, reliable, and standardized way between networks, including internet data traveling from web servers and data centers to user devices. They essentially make it possible for devices to communicate with each other, and that, in turn, allows users to enjoy internet services like the World Wide Web, email, and so on.
Do VPNs protect against protocol-based attacks?
It depends on the nature of the attack. VPNs encrypt your internet data and mask your IP address, which helps to protect against certain types of cyberattacks, like packet sniffing, Domain Name System (DNS) spoofing, man-in-the-middle (MITM) attacks, and distributed denial-of-service (DDoS) attacks. At the same time, VPNs can’t stop protocol-based attacks that occur above the VPN tunnel or within specific service protocols, including Transport Layer Security (TLS) / Secure Sockets Layer (SSL) downgrade attacks or application-layer exploits.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN