What is cyber threat hunting, and how does it work?
A virus or malware that infects your system doesn’t always attack right away. Advanced and targeted threats can lie dormant, collecting data, searching for sensitive information, or stealing credentials that allow them to move laterally across the environment. This kind of activity can continue for weeks or months without triggering obvious alerts.
Finding and removing a threat before it reaches that stage can prevent serious operational and financial damage. That’s why cyber threat hunting is an essential security practice.
In this article, we explore how cyber threat hunting works, the popular methodologies and techniques, and the tools that support effective hunts.
What is cyber threat hunting?
Cyber threat hunting starts with the concept of the assumed breach: the assumption that a cyberattack has already bypassed defenses and introduced malicious code or malware into the system. The goal is to find and remove that threat before it causes your organization any real damage.
Threat hunters are human cybersecurity analysts with a particular skill set who can dig through the entire network and find suspicious behavior that automated systems may miss. This includes subtle indicators of compromise, early-stage lateral movement, or misuse of legitimate credentials.
This approach is necessary because many modern attacks are designed to blend in. Once attackers breach an organization’s systems, they often disguise their activity as normal behavior and evade signature-based detection for extended periods. Identifying and safely removing these threats requires familiarity with the organization’s network and tools that support deep investigation rather than simple alerts.
How cyber threat hunting differs from traditional security
Traditional security tools, such as antivirus software and firewalls, focus on detection and response. They wait for alerts, flag suspicious activity, and react when a predefined condition is met. Cyber threat hunting, on the other hand, proactively searches for threats before they can cause damage.
Proactive vs. reactive security approaches
Reactive security focuses on preventing known threats. It follows predefined rules, signatures, and indicators of compromise to detect malicious activity after it occurs. This approach works well with common attack patterns, known vulnerabilities, and malware with identifiable signatures.
However, reactive security doesn’t know how to detect unknown threats such as:
- Zero-day vulnerabilities: Unknown and unpatched software weaknesses that attackers can exploit immediately.
- Advanced persistent threats (APTs): Stealthy, long-term attacks where intruders maintain access to a network to steal data or monitor activity.
- Novel attack techniques: New or rare methods of breaching systems that haven’t been recognized or blocked by security tools.
These threats often evade traditional detection methods and may remain active inside a network for long periods.
Cyber threat hunting takes a different approach. It assumes an attack on the system already happened, then makes educated assumptions about the potential injection of malicious files by the attacker. Threat hunters then operate inside the environment and actively investigate to confirm or disprove these assumptions.
For example, a threat hunter might hypothesize that an attacker is abusing PowerShell to move laterally between systems. Instead of waiting for an alert, the hunter analyzes logs, endpoint activity, and network traffic to find evidence that supports or contradicts that theory.
Threat hunting vs. automated threat detection
Threat detection relies heavily on automation. Security tools continuously analyze large volumes of data and generate alerts when activity matches predefined rules or known attack patterns. This approach is fast, scalable, and effective at identifying repeatable threats.
Threat hunting also uses automated tools, but the role of automation is different. Tools collect and organize data, while human analysts interpret it. Instead of responding to alerts, threat hunters look for patterns, anomalies, and behaviors that suggest something may be wrong, even when systems report everything is normal.
This human-driven analysis allows hunters to spot subtle signals that automated detection may miss, such as unusual login behavior, unexpected privilege use, or abnormal file movement.
Threat hunting vs. SOC responsibilities
Threat hunting is not a separate function from the security operations center (SOC). When performed within a SOC, it uses the same data sources and tools but follows a different objective. The SOC reacts to what security systems detect, while threat hunting looks for what those systems may miss.
SOC responsibilities focus on operational security tasks, including:
- Monitoring security alerts across tools and platforms.
- Triaging alerts to separate false positives from real threats.
- Investigating confirmed security events.
- Containing incidents and supporting remediation.
- Updating incident response reports to prepare for future attacks.
Threat hunting responsibilities focus on proactive investigation, including:
- Searching for malicious activity that hasn’t triggered alerts.
- Investigating suspicious behavior that may have appeared legitimate at first glance.
- Testing assumptions about attacker presence and movement.
- Identifying gaps in detection and visibility.
- Feeding findings back into detection rules and SOC workflows.
In security programs with defined processes, both roles reinforce each other. SOC operations handle real-time response, while threat hunting improves detection quality, reduces blind spots, and shortens attacker dwell time.
| Threat hunting | Reactive security | Automated threat detection | SOC operations | |
| Primary focus | Proactively finding hidden threats | Responding to known threats | Identifying threats at scale | Monitoring and incident response |
| Trigger for action | Analyst hypothesis | Security alerts | Rules or signatures | Alert or security event |
| Role of humans | Lead investigations and analysis | Validate alerts and respond | Review alerts and escalate | Investigate and contain incidents |
| Threat types detected | Unknown threats; APTs; stealthy attacker behavior | Known malware; common attack patterns | Known indicators of compromise | Confirmed security incidents |
How cyber threat hunting works in practice
Cyber threat hunting follows a structured workflow. Analysts actively search for signs of malicious activity by forming hypotheses, examining relevant data, and validating findings before feeding results back into security operations. The goal is not to confirm alerts but to uncover threats that have avoided detection.
Forming hypotheses and investigative questions
Threat hunting typically begins with a hypothesis. Hunters start with an assumption about how an attacker might operate inside the environment and then test that assumption using available data.
Hypotheses can come from:
- Knowledge of attacker tactics and recent campaigns.
- Newly disclosed vulnerabilities or exploits.
- Unusual patterns observed in logs or telemetry.
- Intelligence shared internally or by trusted sources.
To refine a hypothesis, threat hunters ask targeted investigative questions, such as:
- Are any systems communicating in ways that don’t match their normal role?
- Are legitimate tools being used in unusual or high-risk ways?
- Do authentication patterns suggest credential misuse or privilege escalation?
- Has activity changed after a patch, configuration update, or external event?
Once the hypothesis and scope are defined, the hunt focuses on collecting evidence that either supports or disproves the assumption. It’s important to note, however, that smaller organizations might not have the baseline data to support all these questions and will need to be selective.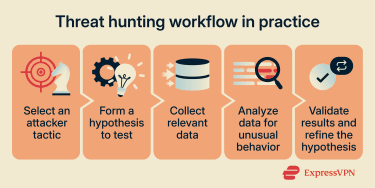
Analyzing data and identifying suspicious behavior
With a hypothesis in place, the threat hunters investigate the network and system, looking for behaviors that deviate from established baselines. This can include endpoint activity, network traffic, authentication logs, and application telemetry.
Automated analytics and machine learning (ML) can help detect irregular patterns across large data sets, but human analysis remains essential. Threat hunters interpret context, correlate events, and determine whether unusual behavior reflects malicious intent or legitimate operational activity.
At this stage, threat hunters can often spot early indicators of compromise, stealthy attacker movement, or abuse of trusted tools. By identifying these signals before alerts trigger, they can detect APTs earlier in their lifecycle.
Validating findings and improving defenses
Not every anomaly represents a real threat. Threat hunters must validate findings before escalating them. This validation may involve forensic analysis, controlled execution in a sandbox, or cross-checking activity against trusted threat intelligence.
Once they confirm the malicious activity, it gets escalated for containment and remediation. What’s more, everything must be documented, as insights from successful hunts often lead to improved detection rules, better alert tuning, and stronger defensive controls.
By integrating threat hunting outcomes into daily security operations, organizations reduce blind spots and improve their ability to detect similar activity in the future.
Common threat hunting methodologies
Threat hunting doesn't follow a single formula. Teams use different methodologies depending on their goals, available data, and threat landscape. Most hunting programs rely on a combination of hypothesis-driven, indicator-based, and behavioral approaches.
Many threat hunting teams use the MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework to structure these approaches. ATT&CK catalogs real-world threat tactics and techniques across the attack lifecycle, giving threat hunters a standardized way to model behavior, build hypotheses, and map findings to established threat patterns.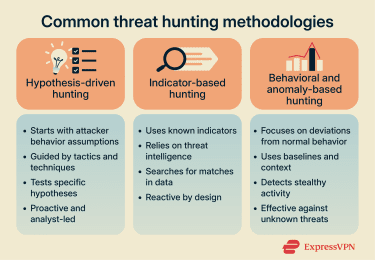
Hypothesis-driven threat hunting
Hypothesis-driven threat hunting is a proactive methodology that starts with an informed assumption about attacker behavior. Threat hunters form hypotheses based on knowledge of real-world attacks, attacker tactics, techniques and procedures, and frameworks.
A hypothesis might focus on how attackers typically exploit a specific weakness or misuse legitimate tools. From there, the hunter defines what evidence would support or refute that assumption and begins collecting relevant data.
This process typically involves:
- Identifying attacker behaviors or techniques to investigate.
- Gathering relevant telemetry such as logs, endpoint activity, and network data.
- Analyzing that data to confirm or reject the hypothesis.
- Determining next steps if malicious activity is found.
Indicator-based threat hunting
While hypothesis-driven hunting is the preferred “core” methodology, indicator-based threat hunting is also used, where known indicators guide investigations. These indicators often come from threat intelligence feeds, past incidents, or external reporting and include:
- Malicious file hashes.
- Suspicious IP addresses or domains.
- Known command-and-control infrastructure.
Some hunts also incorporate indicators of attack, which describe attacker behavior and intent rather than static artifacts.
Indicator-based hunting is more reactive than hypothesis-driven hunting because it depends on prior knowledge of threats. Once hunters identify matching indicators in their environment, they investigate related activity to determine whether a compromise has occurred, how far it spread, and which data may be affected.
While this methodology is effective for identifying known threats, it’s less reliable than hypothesis-driven hunting when it comes to novel attacks that leave no recognizable indicators. In other words, it complements the hypothesis-based approach rather than replacing it.
Behavioral and anomaly-based hunting
Behavioral and anomaly-based hunting focuses on detecting activity that deviates from established norms. Instead of searching for known indicators, hunters search for unusual patterns in how users, systems, and applications behave.
Behavioral baselines are built from historical data such as login behavior, file access patterns, network flows, and privilege use. When activity falls outside expected patterns, it becomes a lead for investigation.
For example, abnormal login locations, unexpected data transfers, or privilege escalation that doesn't align with a user’s role can indicate compromised credentials or insider misuse.
This methodology is especially effective against modern attacks that rely on legitimate tools and stolen credentials.
Threat hunting tools and data sources
Threat hunters rely on a combination of tools and data sources to support their investigations. These tools provide visibility across systems, helping analysts collect and analyze activity that may indicate malicious behavior. While tools don’t replace human judgment, they’re essential for scaling threat hunting efforts across complex environments.
SIEM, EDR, and XDR platforms
Threat hunting commonly relies on platforms that aggregate and correlate security data from across the organization. Each security platform plays a different role in providing visibility and investigative context.
- Security information and event management (SIEM): SIEM platforms gather and standardize data from a variety of sources, including servers, applications, network devices, and security tools. By correlating events in near real time, SIEM systems help threat hunters identify patterns, anomalies, and sequences of activity that may point to a potential threat.
- Endpoint detection and response (EDR): EDR tools monitor activity on end-user devices and servers, giving threat hunters detailed visibility into processes, file changes, command execution, and user behavior at the endpoint level. This data helps analysts investigate suspicious activity, trace attacker actions, and understand how a threat operates inside individual systems.
- Extended detection and response (XDR): XDR platforms combine telemetry from endpoints, networks, email, and cloud environments into a unified view. Threat hunters use XDR to correlate activity across multiple domains, improve investigation efficiency, and gain broader visibility into attacks that span different parts of the environment.
Log analysis and threat intelligence feeds
Log analysis and threat intelligence provide the raw material that threat hunters need to identify suspicious behavior and validate findings. Logs capture detailed records of system activity, while threat intelligence adds external context about known threats and attacker behavior.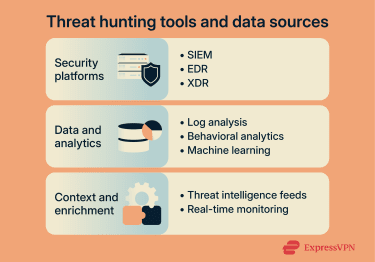
Advanced analytics help uncover meaningful signals from large volumes of data. Using statistical methods, behavioral modeling, and ML, analytics engines can spot unusual action patterns that need further examination.
Automation within this process reduces manual effort and shortens the time it takes to uncover potential threats. Analysts can drill into correlated events, test new hypotheses, and iteratively search for less obvious attacker activity.
Threat intelligence integration helps by linking what is seen inside the organization with information from outside, such as signs of a security breach, how attackers work, and new threats. This context helps threat hunters prioritize investigations, reduce false positives, and better understand the intent and sophistication of potential threats.
Core principles behind effective threat hunting
Effective threat hunting depends as much on people and process as it does on technology. Tools provide visibility, but hunters need the expertise, context, and discipline to interpret what they see and act on it correctly.
Why threat hunting requires skilled teams and resources
Threat hunters are more than just security experts; they must understand the environment they’re protecting. That includes system architecture, network communication flows, identity and access controls, and where sensitive data lives. Without this context, it becomes difficult to distinguish legitimate activity from malicious behavior.
Hunters also need insight into how the business operates. Understanding normal employee behavior and customer usage patterns helps analysts recognize activity that falls outside expected norms. An action may appear suspicious in isolation but prove harmless once the business context is applied, or vice versa.
Establishing behavioral baselines plays a key role here. For example, unusually high traffic to a rarely used feature or system may indicate reconnaissance, data scraping, or early-stage exploitation.
Access to comprehensive data is equally important. Threat hunters rely on centralized logging and telemetry from across the environment to conduct effective investigations. Network devices, firewalls, endpoint tools, and intrusion detection systems all contribute data that helps hunters reconstruct activity and identify subtle attack patterns.
Continuous learning, documentation, and knowledge sharing
Threat hunting isn’t static. Attack techniques evolve constantly, and hunters need to stay informed about new tactics and technology. Relying on outdated threat information or well-known indicators is useless, because threat defenders often block these threats automatically anyway.
Today’s hunts focus on behaviors rather than obvious artifacts. Attackers increasingly exploit zero-day vulnerabilities, abuse legitimate credentials, and combine techniques across systems to evade detection. Identifying these threats requires continuous learning and exposure to up-to-date research, threat intelligence, and incident analysis.
Documentation and knowledge sharing help turn individual hunts into lasting improvements. Recording hypotheses, findings, and outcomes allows teams to refine detection rules, improve future investigations, and reduce repeated effort. Sharing this knowledge across security teams strengthens overall defenses and ensures lessons learned don’t remain siloed.
Challenges and limitations of threat hunting
Threat hunting offers clear benefits, but it also comes with practical limitations. Organizations need to set realistic expectations and build programs that are sustainable over time.
Skills gaps and resource constraints
Effective threat hunting requires experienced analysts who understand attacker behavior, system architecture, and data analysis. These skills take time to develop and are in short supply across the cybersecurity industry, making it difficult for many organizations to build and sustain dedicated hunting capabilities.
Resource constraints can limit threat hunting efforts. Teams often need to balance proactive investigations with reactive responsibilities such as alert triage and incident response. In smaller environments, limited visibility, incomplete telemetry, or restricted tooling can reduce the scope of hunts. While threat hunting can still provide value, it typically requires careful scoping and clear priorities.
For organizations that lack in-house resources, managed threat hunting services can help bridge the gap. These services offer access to skilled analysts, advanced tools, and continuous monitoring, eliminating the need for a dedicated in-house team.
Keeping up with evolving threats
Attack techniques evolve constantly as threat actors adapt to bypass defenses. Threat hunting approaches that aren’t regularly updated can quickly become obsolete.
There’s often a delay between the emergence of new attack techniques and reliable detection. During that gap, hunters may rely on limited context or indirect signals, which increases the risk of false positives or missed activity. Continuous testing and refinement help keep threat hunting aligned with a changing threat landscape.
FAQ: Common questions about cyber threat hunting
When should an organization start threat hunting?
Organizations should start threat hunting once they have basic security visibility in place, such as centralized logging and endpoint telemetry. Threat hunting is particularly valuable for uncovering hidden threats and verifying that existing security controls are effective. It doesn't require a fully mature security program to begin, but it does require a clear scope and realistic expectations.
Can small teams do threat hunting without a full SOC?
Threat hunting doesn't require a full security operations center (SOC). Small teams can conduct focused hunts using centralized logs, endpoint data, and cloud-based security tools. The key is scoping hunts carefully and prioritizing high-risk systems or behaviors. While limited resources may restrict hunt depth or frequency, even targeted hunting can uncover threats that automated detection misses.
Is threat hunting possible without EDR or XDR?
Threat hunting is a human-led investigative process, and it doesn't strictly depend on endpoint detection and response (EDR) or extended detection and response (XDR) platforms. These tools improve visibility and speed, but hunters can still conduct effective investigations using logs, network data, identity records, and other telemetry. The quality and completeness of available data matter more than the specific platform.
How often should threat hunting be performed?
Threat hunting frequency depends on risk tolerance and available resources. Some organizations run continuous, automated hunts and supplement them with periodic manual investigations. Others perform scheduled hunts weekly or monthly. Even occasional hunts can provide value if they focus on realistic threat scenarios and high-impact assets.
What skills does a threat hunter need?
Effective threat hunters combine technical expertise, investigative thinking, and knowledge of the organization they’re protecting. This includes understanding operating systems, attacker tactics, workflows, and threat intelligence, strong data analysis, and scripting skills.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN