-
What is the SMB protocol? (Server Message Block explained)
If you open a spreadsheet from a shared drive, send a document to a network printer, or even sync a backup to network attached storage (NAS), you’re likely using the Server Message Block (SMB) proto...
-

Loopback address: What it is and how to use it
A loopback address is a way for a computer to talk to itself. Instead of being sent outward, data directed to a loopback address returns to the same device. This can be a useful tool for testing appli...
-

How to permanently delete your Reddit account
If you’ve decided it’s time to leave Reddit, whether to improve your online privacy, as part of a break from social media, or just because you don’t use it anymore, deleting your account is quic...
-

What is a site-to-site VPN, and how does it work?
When businesses operate across different offices, countries, and time zones, keeping networks connected and secure can be challenging. A site-to-site virtual private network (VPN) helps by creating an...
-

What is a walled garden?
A walled garden is a digital environment managed by a single tech company, such as Apple or Meta. Within this closed space, the company controls what users can access, how data is shared, and which ap...
-

How to detect and remove spyware on iPhone (complete security guide)
Your iPhone holds more than just your apps and messages. It’s a central hub for your photos, financial information, and private conversations, making it a valuable target for spyware. Spyware can st...
-

What is MU-MIMO, and why does it matter for VPN performance?
Wi-Fi has come a long way from the days when only one device could get a clear signal at a time. Today, with dozens of connected devices in most homes, from phones and laptops to smart TVs and cameras...
-
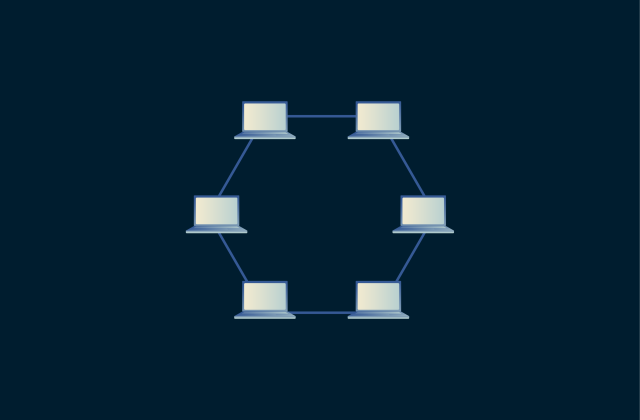
Network topology: Best practices for modern networks
A well-designed network starts with a clear understanding of its structure. Network topology is the blueprint of how devices and connections interact, and it plays a key role in determining a network�...
-

How does the internet work?
Billions of people use the internet daily for everything from work to shopping, banking, entertainment, and keeping in touch with family and friends. It’s an integral, essential part of everyday lif...
-

Google critical security alert: How to recognize and respond
Getting a Google security alert may be alarming, but it doesn’t automatically mean your account is in danger. Sometimes, you might trigger one yourself by, for example, signing in from a new device....
Featured





